The cyber threat landscape has evolved, and among the most unsettling developments is the “Harvest Now, Decrypt Later” (HNDL) attack. This strategy is not only a technical concern for security experts but also a crucial policy and future-readiness issue for governments, enterprises, and even individuals. Here’s a comprehensive look at what HNDL means, how it works, and its far-reaching consequences.
What Is "Harvest Now, Decrypt Later"?
Harvest Now, Decrypt Later (sometimes called “store now, decrypt later”) is a method used by cybercriminals and state-level threat actors. They intercept or steal encrypted data now, knowing they cannot currently break the encryption. Rather than giving up, they simply store these encrypted files, emails, communications, and other data securely, waiting until some future technological breakthrough, particularly the rise of quantum computing makes decryption possible.
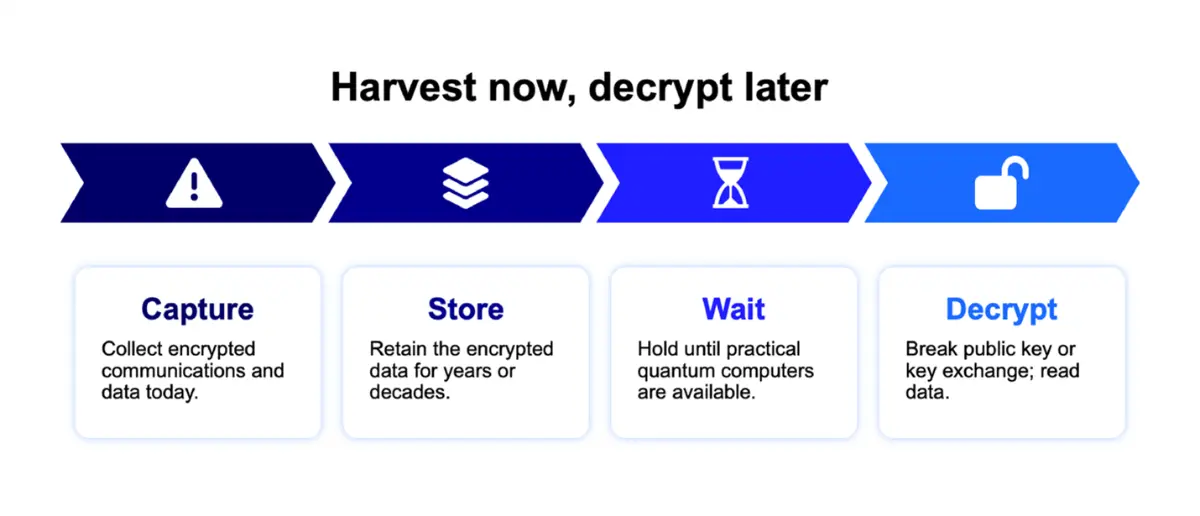
How Does It Work?
An HNDL attack unfolds over a long timeline and typically proceeds through three stages:
First, attackers gather as much encrypted information as possible. This data can come from network eavesdropping, breaching secure storage, copying encrypted backups, or surveilling communication channels. Importantly, they don’t have to decrypt the data now; their aim is simply to collect and archive it.
Second, attackers patiently wait, possibly for many years. During this time, quantum computing and advanced algorithms are being developed that, unlike today’s computers, could rapidly break classic encryption standards like RSA and ECC.
Finally, once capable technology is in their hands, threat actors revisit their private data troves and use advanced means to decrypt what was previously considered secure. This gives them access to long-held secrets, potentially opening up sensitive government information, corporate trade secrets, private messages, medical records, or intellectual property from the past.
Why Does It Matter for the Future?
This threat is serious because today’s encrypted data has a long shelf-life, medical histories, confidential communications, or financial records could remain valuable even decades from now. What seems unbreakable today may be routine to decrypt tomorrow.
Quantum computing represents the single biggest risk to encryption. Quantum computers can efficiently solve the mathematical problems underlying traditional cryptography, such as factoring large numbers (key to breaking RSA), rendering today’s defenses obsolete once these quantum machines become practical.
Hidden and Ongoing Risk
HNDL is especially insidious because victims may never realize their data was targeted. There are usually no warning signs or immediate consequences. Attackers may collect terabytes of encrypted files over years, waiting for the right moment. Sensitive data could thus be compromised quietly and en masse, with long-term consequences for privacy, business, and national security.
The prospect of Q-Day - the unknown moment when quantum computers can break widely used encryption is a ticking clock. Every day that organizations delay adopting new standards means more data may be quietly harvested and stored for future exploitation.
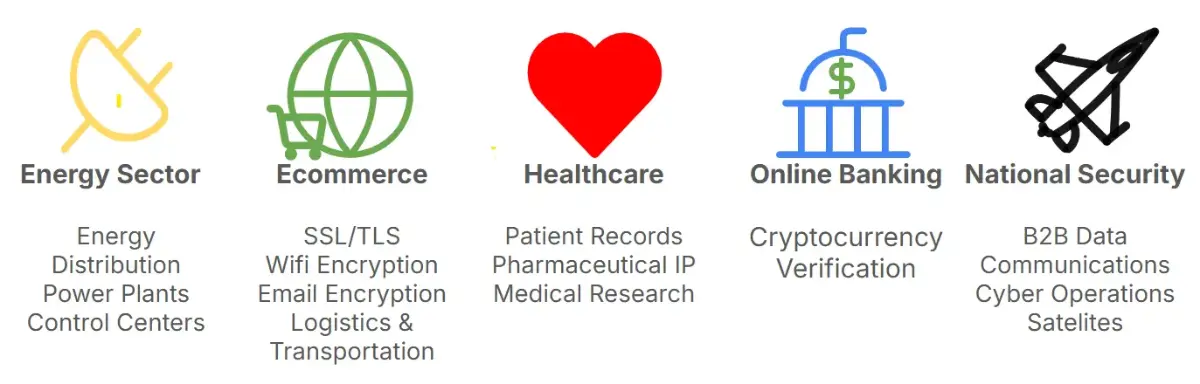
Who Is at Risk?
Everyone from large enterprises to small businesses, individuals to critical infrastructure, can be targeted. Institutions that handle information with a long useful life, such as healthcare, defense, technology, or government, are especially vulnerable. Even organizations using strong encryption may find themselves exposed if they don’t plan for the quantum future.
Defense and Mitigation
To counter HNDL attacks, organizations and policymakers must act now:
- Move to quantum-resistant encryption: Start the transition to algorithms designed to withstand quantum attacks.
- Implement forward secrecy: Use encryption that creates temporary keys for each session, limiting damage if one is broken in the future.
- Routinely re-encrypt old data: Regularly re-secure archives with the latest, strongest algorithms.
- Monitor and audit for leaks: Stay vigilant for signs of large-scale data harvesting or eavesdropping, even if data is currently protected.
- Update legal and regulatory frameworks: Governments should adjust data protection laws to address the long-term risks of HNDL.
Final Thoughts
Harvest Now, Decrypt Later is not science fiction. It is already happening with every encrypted message intercepted, every secured document stolen, and every backup copied by threat actors focused on the future. Long-term vigilance, technical innovation, and proactive policy are the keys to securing our digital world both now and for generations to come. It’s not just about protecting secrets today, but ensuring they remain safe tomorrow, and for decades after.


Discussion
Start the conversation
No comments yet
Be the first to share your thoughts on this article. Your insights could spark an interesting discussion!