
Apple's $1 Billion Bet on Google's Gemini: A Strategic Shift in Siri's AI Future
In a move that signals a significant departure from its traditional self-reliant approach to technology, Apple is on the verge of finalizing a deal wo...

In a move that signals a significant departure from its traditional self-reliant approach to technology, Apple is on the verge of finalizing a deal wo...
Artificial intelligence is becoming a ubiquitous part of our daily interactions, powering everything from chatbots to virtual assistants and content m...
...
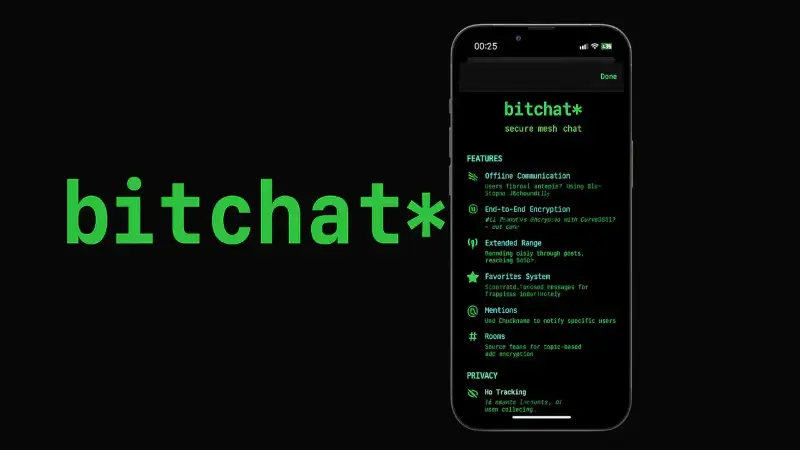
In July 2025, Jack Dorsey officially launched the beta version of Bitchat, a groundbreaking messaging app that operates entirely offline, marking a si...

The Earth Has Eyes NowImagine a machine that sees the Earth not just as it is but as it was, and as it will be.It knows when a rainforest breathes bac...
...

A staggering scandal has erupted in the cryptocurrency world as a $14.5 billion Bitcoin theft, quietly orchestrated nearly five years ago, has finally...
...

In a landmark move to address the growing concern of AI-enabled academic dishonesty, OpenAI has unveiled a new feature within ChatGPT - Study Mode. De...
...

In a world where customer expectations are rising faster than ever, Zomato has pulled off something extraordinary and quietly transformative. With the...
...

OpenAI is preparing for the highly anticipated release of its next-generation artificial intelligence model, GPT‑5, scheduled for early August 2025. M...

A New Era of Urban Logistics Begins UndergroundIn a bold step toward redefining city logistics, the city of Shenzhen has launched a fleet of penguin-s...
...

In July 2025, Amazon Web Services (AWS) introduced Kiro, a next-generation agentic AI IDE designed to bring order to the chaos of “vibe coding.” More ...
...

What if your GPU didn’t have to render every pixel but could still deliver visuals that look better than reality?That’s exactly what NVIDIA is doing w...
...

Artificial intelligence has become the latest buzzword in nearly every industry, and networking is no exception. From AI-powered switches to self-driv...

What is n8n 🤔???It is a workflow automation tool that allows you to connect apps, services, and APIs without writing much (or any) code. It stands fo...

The field of computing has evolved dramatically over the past century, from the mechanical devices of the 1930s to today’s advanced processors. Here’s...

IntroductionIn today's digital age, artificial intelligence (AI) has become an integral part of our lives. However, with the increasing concerns about...
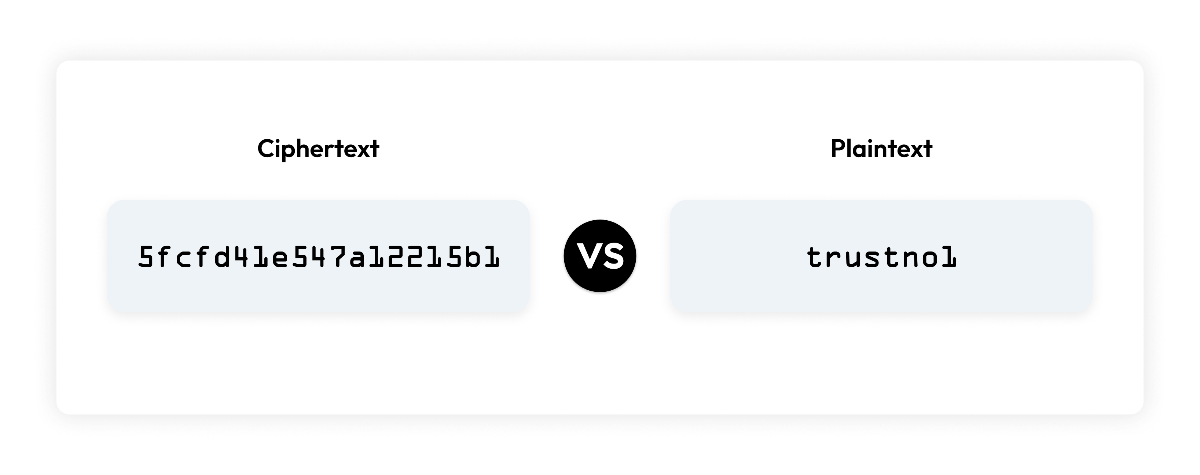
What is a Cipher?A cipher is the encoding or encrypting of a message in a manner that only those with the key or decoding method will be able to read ...

In the realm of operating systems, Windows and Linux stand out as two of the most widely used platforms. This blog will explore the key differences be...
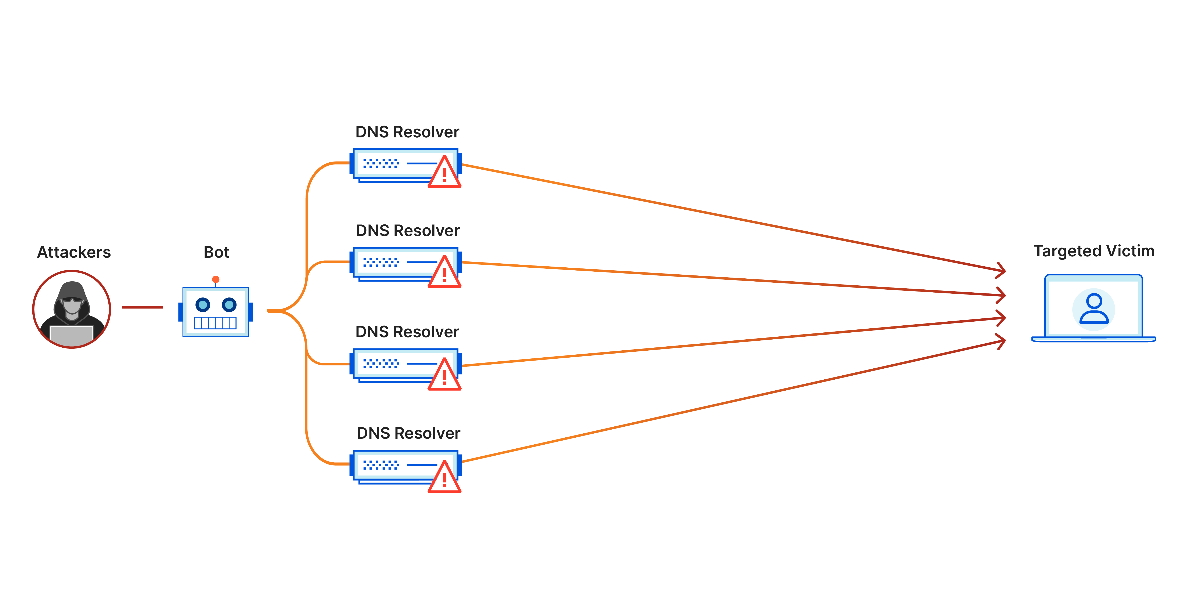
DDoS attacks, or Distributed Denial of Service attacks, are a growing concern in the digital landscape. Imagine a bustling highway suddenly choked wit...

Common cryptographic algorithms may no longer be considered secure under future quantum computers, which will cause a serious threat to network securi...

In our increasingly digital lives, keeping our online accounts secure is more crucial than ever. One of the most effective ways to bolster your accoun...

C++ has emerged as a powerful language in the realm of operating system development, combining the efficiency of C with advanced programming paradigms...

When you enter a URL into your browser, it’s easy to overlook the small but significant "HTTP" or "HTTPS" prefix that often appears. These prefixes ar...
In today's digital landscape, web security is a critical concern for anyone with an online presence. From developers to business owners, understanding...

In today's data-focused world, having a good storage system is very important. Network Attached Storage (NAS) systems are useful for storing, organizi...

Networking, in the context of information technology, refers to the practice of connecting computers and other devices to share resources and informat...

In today's digital era, the importance of cybersecurity cannot be overstated, especially for multinational corporations (MNCs) that operate across var...

In the world of digital dangers, cyber attackers come in many forms, including individuals and groups with different goals and ways of operating. Unde...

Malware is a software designed to harm devices and networks. Primary purpose of malware is to obtain money, or in some cases and intelligence advantag...

Welcome to our professional discourse on the Certified Information Systems Security Professional (CISSP) certification, esteemed readers! Those famili...

In today's fast-moving digital world, where technology is everywhere, online security is very important. There are many dangers online, but one of the...

In today's world, AI tools like ChatGPT, Gemini, and Blackbox AI have rapidly evolved our pace of working. To maximize their effectiveness and accurac...

CrowdStrike, a prominent name in cybersecurity, has recently experienced a notable dip in its stock price. On July 10, 2024, the company's shares fell...

As we navigate through the ever-evolving technology landscape, we encounter the fascinating realm of Artificial Intelligence, affectionately known as ...

In the vast ocean of technology, Linux stands as a beacon for those seeking a versatile, secure, and powerful operating system. Whether you're a tech ...